Malware is just a term that refers to all software that has been designed for malicious purposes and therefore it is impossible to know how much Malware there are today. A wide variety of malware is known to exist and they work differently. These can take control of the software and hardware of the computer or device that they have managed to infect and, in this way, can access and put user information at risk.

Companies that produce software and hardware are aware of the existence of malware and do their best to prevent their products from having vulnerabilities that allow malware to access user data, however, this is not always successfully avoided. This is one of the main reasons that companies distribute updates to their software constantly. However, it is a fact that what most puts a user's information at risk is the user himself. This happens due to minor oversights and manipulation techniques by cybercriminals.
In this article
Part 1. How Does Adversary Use Malware to Target Me
It is impossible to know exactly how many Malware exists today but it is known that there are only two means of Malware infection.
Through the internet
It is necessary to be careful as a public or private network may have previously been intervened by an attacker, so you should not connect to an unknown network. In addition, it is known that the most common method of infection is through deception or engineering strategies social networks that lead people to voluntarily download malware, for example: via email attachments, windows that pop up while browsing, or even spoofed websites.
Through physical interaction
This can happen when a person connects a storage device, as it may have been previously infected and, when connecting it to your computer, it can be infected if there is no protection system to prevent it. However, it is important to keep in mind that security systems that protect against attacks by malicious software are not foolproof. These security systems are designed based on the millions of malware that have been successfully identified so far. In other words, these security systems may not detect a threat if it is highly sophisticated malware. For this reason, it is increasingly common to become aware of the risks of surfing the Internet and the precautionary measures that can avoid being the victim of an attack.
Part 2. How to Protect Computer Against Malware
Even though cyber security is not a new topic, it had never been such an important issue before it was now. Companies that specialize in computer security have reported that from 2020 to 2021, the number of cases of cyber-attacks has increased by at least 600%, with emails being the origin of at least 92% of these cases.
Today more than ever before, it is important to take prevention measures. Next, I will talk about some ways to protect your computer and personal information from attackers.
1. Keep up to date
According to the collected data provided by the developer companies of malware protection systems mention that 75% of infections occur on computers that have an outdated protection system. Make sure your operating system is always updated.
2. Antivirus software
There is dozens of antivirus that can help you protect your computer. Some of them are free and offer a high level of protection, on the other hand, you can also choose to pay for a premium antivirus as these usually offer additional benefits such as email analysis and assisted web browsing.
3. Antispyware software
A virus and spyware are not the same, but they are very similar. The biggest difference between spyware and viruses is that viruses can reproduce themselves and can spread from one computer to another while spyware stays on your computer. In general, antivirus is able to detect them, but before taking this for granted, check that your antivirus offers protection against this type of threat.
4. Firewalls
A firewall can be hardware, software, or both at the same time and monitors incoming and outgoing network traffic. This acts as a filter and decides whether to allow or block traffic based on a defined set of security rules, usually defined by your operating system. In general, this feature is usually activated and configured by default, but it is advisable to check that everything is in order.
5. Choose strong passwords
According to the data collected by a company specialized in offering computer security services, they mention that 77% of people admit to using weak passwords, 56% say they never change their passwords and 42.7% of users use the same password for all.
A strong password is not one that has non-alphanumeric characters. A strong password is essentially a long password. Experts recommend using sentences as passwords as they have large amounts of letters and are easier for the user to memorize.
6. Use stronger authentication
User authentication has existed for more than twenty years. Authentication is basically a second filter and consists of confirming that the person who has entered a password is authorized to possess that password. There are at least three different types:
Authentication by knowledge: based on information that only the user knows. Key questions such as: where were you born, the name of your pet, or where did you study.
Membership authentication: based on something the user owns. For example: Using a Smartphone, a Smartwatch, or a key generator.
Authentication by characteristics: based on some physical characteristics of the user. For example A biometric system.
7. Be careful what you click
Everyone has come across an ad that pops up out of nowhere and wants you to accidentally click on it. It is clear that these types of threats are less and less frequent since the browsers themselves block this type of interaction. But nevertheless. Have you ever stopped to look at the bottom of your browser? When you hover your cursor over a clickable element such as a button or a link, it shows the address where it will redirect you without the need for you to click. This is a tedious but very important practice, as it is one of the most effective ways to avoid being a victim of spoofing.
For example "www.google.com" is an official and secure address, while "www.gooogle.com" or "www.gogle.com" are misspelled and this could indicate that it is a spoofed website. Before clicking on a link or button, check that the website it will take you to is safe and well written by hovering over it.
8. Shop safely
Nowadays it is very common to make purchases over the internet. It is usually very easy, fast, and safe. However, you must make sure that the site where you are buying is secure. Remember to check that the web domain name is well spelled and pay attention to the prefix.
HTTP: The acronym HTTP refers to a hypertext transfer protocol. In other words, HTTP is a communication protocol that allows the transfer of information on the Internet.
HTTPS: On the other hand, HTTPS uses a combination of two communication protocols (HTTP + SSL) that makes any type of information transmitted over the network encrypted.
Does this mean that if a page has the HTTPS protocol it is secure?
No. The HTTPS protocol only guarantees that the content travels encrypted. This does not guarantee that the server that collects the data is reliable nor does it guarantee that this information cannot be intercepted, it only guarantees that it will travel encrypted and therefore, if intercepted it would be incomprehensible and indecipherable information.
9. Be careful what you share
Remember that the most dangerous characteristic of a virus is that it can easily replicate and infect all types of files. Most antivirus scan all the documents you send and receive to avoid these types of problems. Even so, it is advisable that you perform the analysis manually to make sure that this process was carried out before sending or opening a file.
10. Back up your computer
Even following all these prevention measures, it is important that you back up your information sporadically. Malware can irreversibly damage the integrity of your operating system and even your hardware.
11. Responding to data breaches
Based on the information collected by the main computer security companies in the United States of America. The two main reasons for data breaches are the negligence of users who voluntarily expose their information and the data management errors of third parties.
It can be said that data breach is a common thing so you could simply protect your most important files by encrypting them. In this way, if they are filtered, they will remain inaccessible to the attacker.
Part 3. How to Protect File with PDFelement
Wondershare PDFelement - PDF Editor is a professional file management tool and its main advantage in terms of security is that it has the ability to protect files through passwords and digital signatures, as well as providing many other management tools that favor all types of users.
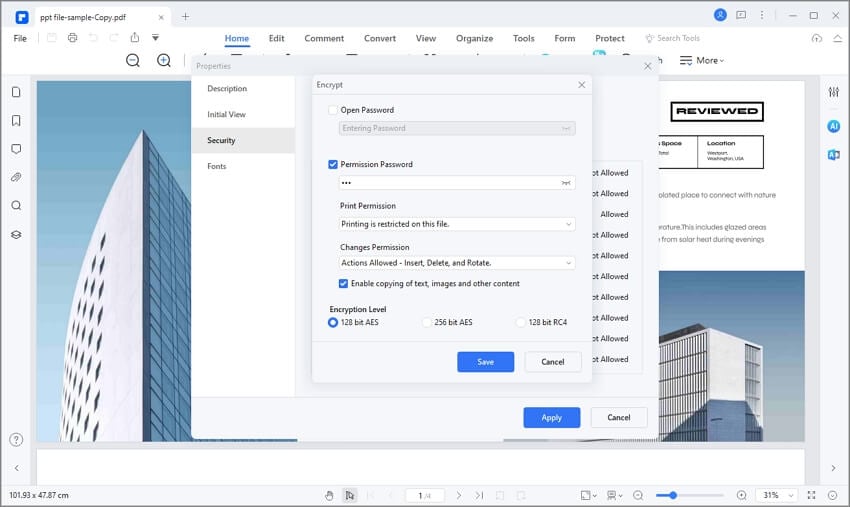
1. Password and Permissions
Password protecting your files will allow you to restrict the reading of anyone who is not authorized to view their content, in addition, you can offer selective permission so that they can only make prints. The information inside will be encrypted until the correct password is entered.
2. Digital Signature
As I mentioned earlier, the most common reason for data breaches today is sending emails, mainly in work environments. This is because most companies distribute newsletters and notifications through this medium. PDFelement offers an online management tool for your files with which you can store and share your files. Information travels, is stored, and reproduced encrypted. In addition, it offers some tools that facilitate the distribution of files in a safe and controlled environment.
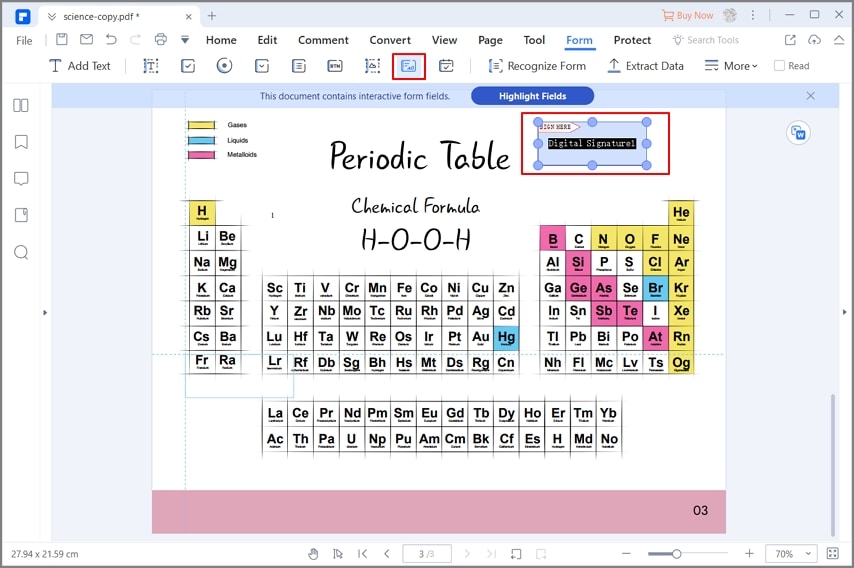
For example: In companies, it is very common to send the same document to all the people in a department just for the purpose of reporting or collecting signatures. With PDFelement, this task becomes extremely easy.
Closing Words
Security is a very important issue. It is estimated that more than 80,000 cyber-attacks occur each day per year. For this reason, it is vitally important not to lower your guard, keep your systems up to date, back up your information and protect it in case of possible breaches. Ideally, you should never be a victim of a cyber-attack, but unfortunately, this may not be up to you alone. Fortunately, by using PDFelement to encrypt your files, you can protect yourself and your team at the same time with great ease.
